Featured
- Get link
- X
- Other Apps
3Nf Decomposition Algorithm Example
3Nf Decomposition Algorithm Example. It guarantees that at least one schema must hold a candidate key for the one being decomposed, which in turn ensures the decomposition generated to be a lossless decomposition. Suppose that x is not a candidate key of t.
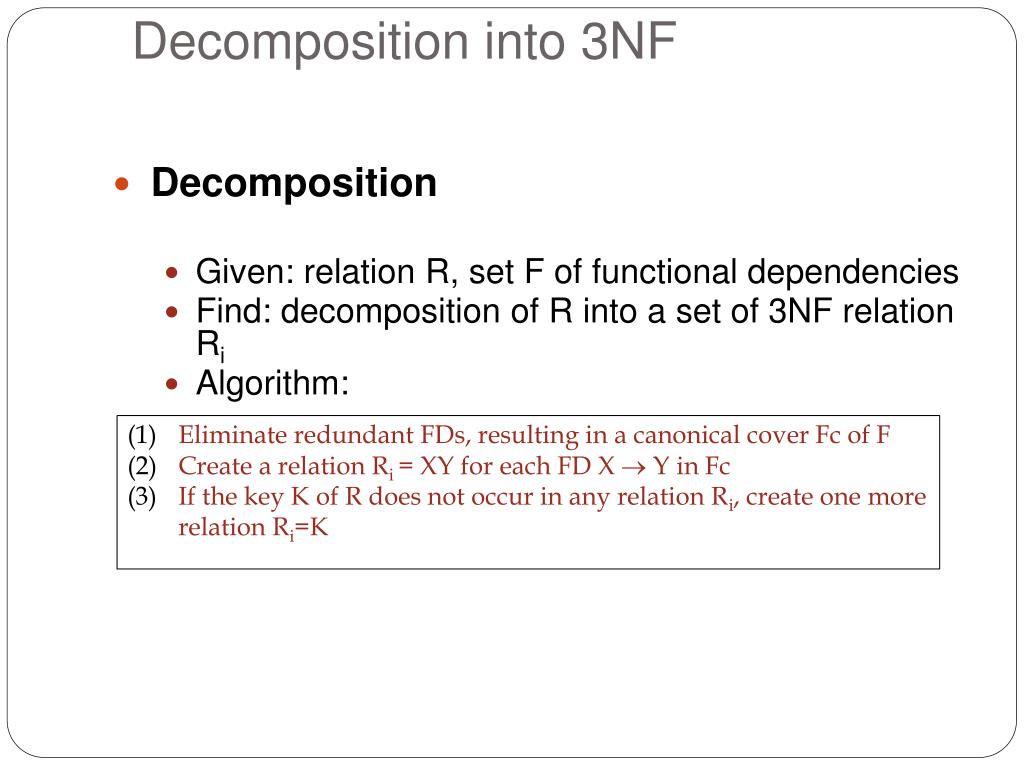
3nf decomposition algorithm let f c be a canonical cover for f i 0 for each from ids 521 at university of illinois, chicago Let t be a table with schema x∪{a}. Third normal form (3nf) decomposition (v) 3nf synthesis algorithm (continued) // step 5:
The Decomposition Algorithm For 3Nf Ensures The Preservation Of Dependencies By Explicitly Building A Schema For Each Dependency In The Canonical Cover.
Find a minimal basis of f, say g; A sample run for 3nf decomposition. For each x!a2fcreate a relation of schema (xa).
3Nf Decomposition Algorithm Let F C Be A Canonical Cover For F I 0 For Each From Ids 521 At University Of Illinois, Chicago
Bcnf (boyce codd normal form) is the advanced version of 3nf. The decomposition algorithm for 3nf ensures the preservation of dependencies by explicitly building a schema for each dependency in the canonical cover. We assume that fis a minimal closure.
Here, R Is Said To Be In Bcnf, If For Every Fd Of The Form Α → Β (Α ⊆ R And Β ⊆ R.) In F + Satisfies One Of The Following Two Conditions:.
(1) eliminate redundant fds, resulting in a canonical cover fc of f (2) create a relation r i = xy for each fd x → y in fc (3) if the key k of r does not occur in any relation r i, create. • we can get both (1) and (2) with a 3nf decomposition. Suppose that x is not a candidate key of t.
Let X → A Be Any Fd In G.
Decomposition of r into a set of 3nf relation r i algorithm: Check wikipedia on armstrong's axioms or functional dependencies and use decomposition, augmentation and decomposition again to obtain ad→c from a→cgh. Then, there exists y ⊂ x such that y → a, namely, y → acan be derived from g.
Return The Decomposition R 1,., R N Together With Their Respective // Sets F 1,., F N Of Fds As The Result Return {(R 1, F 1),., (R N, R N)} Example:
• much better to think in terms of entities and relations • but algorithms are good to know if you encounter redundancy problems 14 Today i read about the 3nf decomposition algorithm. For each fd x → a in g, use {x, a} as the schema of one of the relations in the decomposition;
Popular Posts
True Or False Lsd Is An Example Of A Hallucinogen
- Get link
- X
- Other Apps
Comments
Post a Comment